Port Blocking
Port blocking is a way of preventing users on the LAN from connecting with devices on the WAN via specific services, protocols or applications. It achieves this by permitting or denying traffic from the LAN to pass to the WAN, based on the target port.
Managed Services is the end result of Port Blocking. Managed Services allows you to manage specific services on your network. Furthermore, Managed Services filtering is used to block certain outbound traffic that is directed from a computer or device on the internal network to a specific destination port or port range. In the list of trusted devices, a device entered in the list is excluded from the filtering defined in the service filter table.
Use this screen to configure Port Blocking. You can turn port blocking on or off and configure new and existing Port blocking rules. These can be managed all day, specific says, or specific times.
Click Security > Port Blocking. The following screen displays.
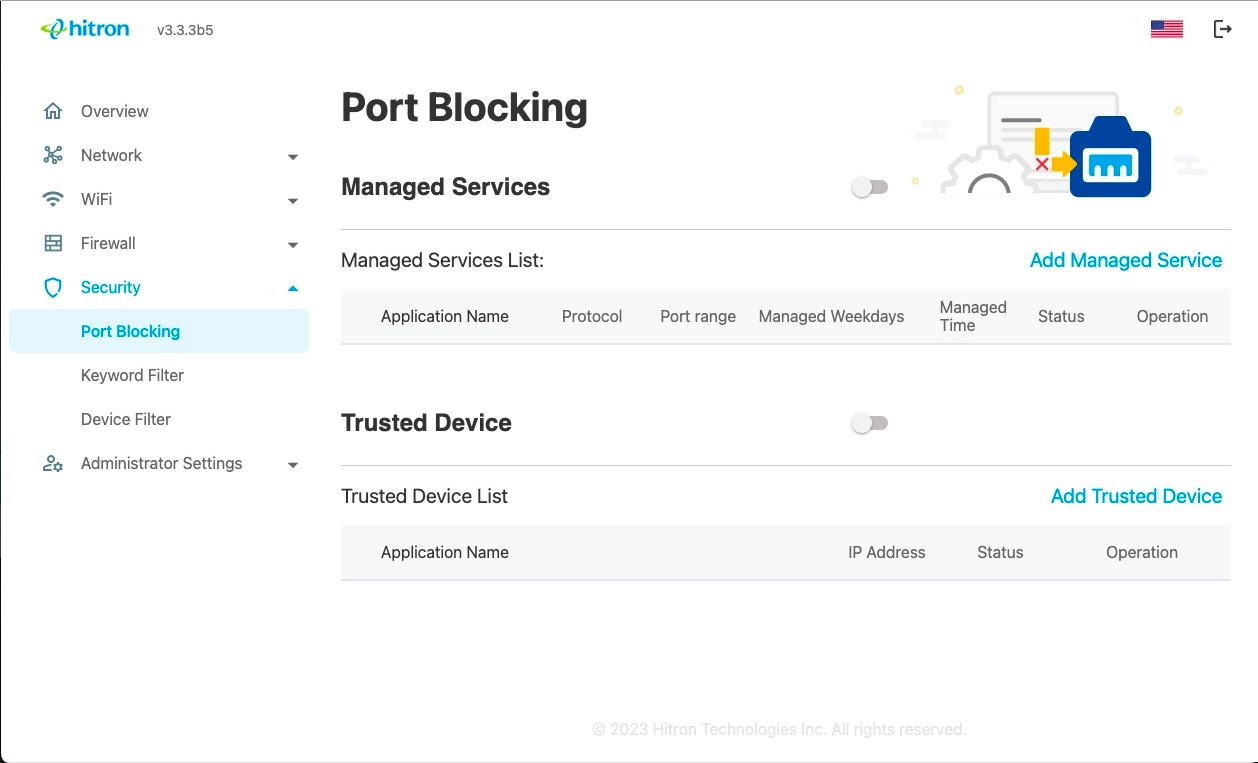
The following table describes the labels in this screen.
• Enable to turn port blocking on.
• Disable to turn port blocking off.
• Transmission Control Protocol (TCP)
• User Datagram Protocol (UDP)
Click to Edit the Rule.
Click to Delete the Rule.
• Enable to turn Trusted Device Rule on.
• Disable to turn Trusted Device Rule off.
Click to Edit the Rule.
Click to Delete the Rule.
Add Managed Service
Managed Services allows you to block the certain applications by blocking its service ports; the function also allows you to block the services by schedule.
Managed Services filtering is used to block certain outbound traffic that is directed from a computer or device on the internal network to a specific destination port or port range. If the filter rule is enabled, users can press the “Add Managed Service” link to add a managed service filter rule. A pop-up window is displayed.
To add a new port blocking rule, click Add Managed Service in the Security > Port Blocking screen.
To edit an existing port blocking rule, locate the rule in the Security > Port Blocking screen and click its button to Edit.
To delete an existing port blocking rule, locate the rule in the Security > Port Blocking screen and click its button to Delete it.
NOTE: Ensure that Port Blocking is Enabled in the Security > Port Blocking screen in order to add or edit port blocking rules.
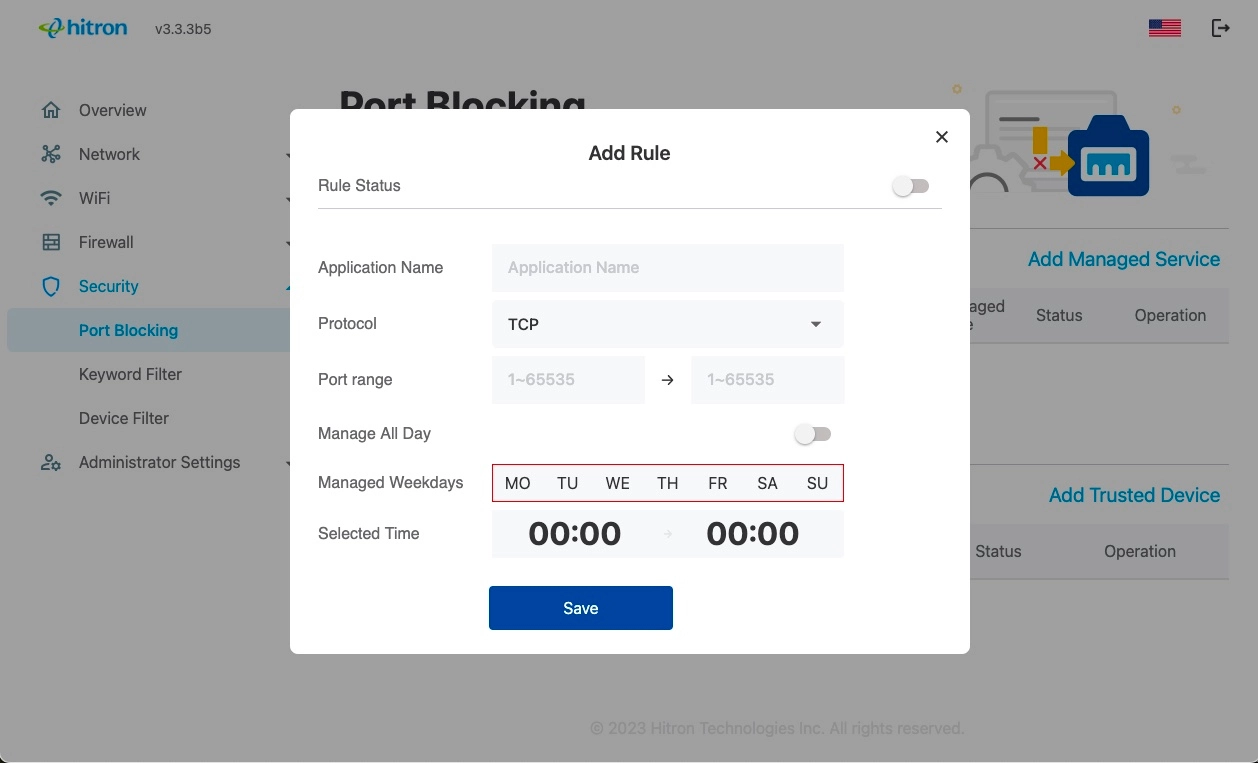
The following table describes the labels in the Add Managed Services screen.
• Enable to activate the trusted device rule.
• Disable to deactivate the trusted device rule.
NOTE: This name is arbitrary, and does not affect functionality in any way.
• Transmission Control Protocol (TCP)
• User Datagram Protocol (UDP)
• Both TCP and UDP (TCP/UDP).
NOTE: If in doubt, leave this field at its default
Enter the start port number in the first field, and the end port number in the second field.
To specify only a single port, enter its number in both fields.
Enable to apply the rule at all times.
Disable to apply the rule only at certain times.
Additional fields display, allowing you to specify the times at which the rule should be applied.
Use the Managed Weekdays fields to specify the days on which the rule should be applied.
A red background indicates that the rule will be applied (traffic will be blocked), and a green background indicates that the rule will not be applied (traffic will not be blocked).
Click a day to toggle the rule on or off for the relevant day.
Enter the start time using twenty-four-hour notation, and enter the end time.
Add Trusted Device
Trusted devices are those to which Managed Services rules are not applied.
To add a new trusted device rule, click Add Trusted Device in the Security > Port Blocking screen.
To edit an existing trusted device rule, locate the rule in the Security > Port Blocking screen and click its button to Edit.
To delete an existing trusted device rule, locate the rule in the Security > Port Blocking screen and click its button to Delete it.
The following screen displays.
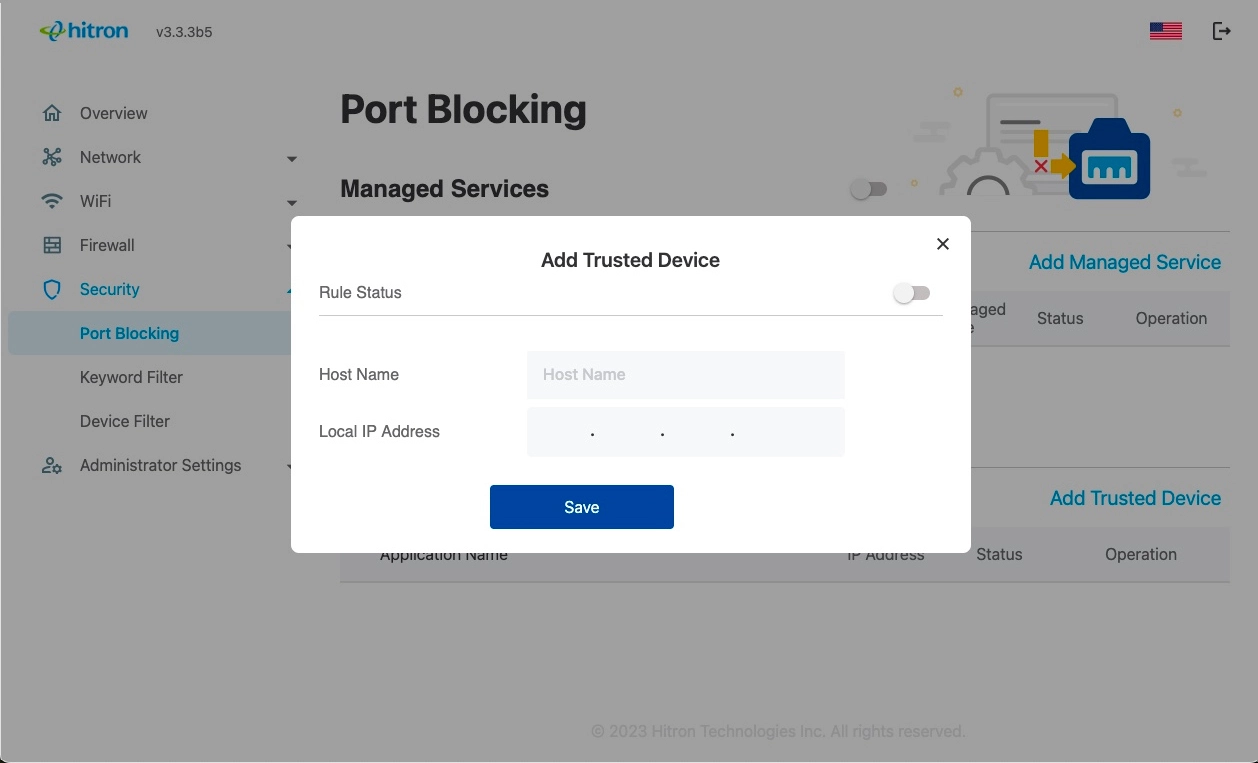
• Enable to activate the trusted device rule.
• Disable to deactivate the trusted device rule.